Exploit Db Api
Then create database and exploits table using the sql file.

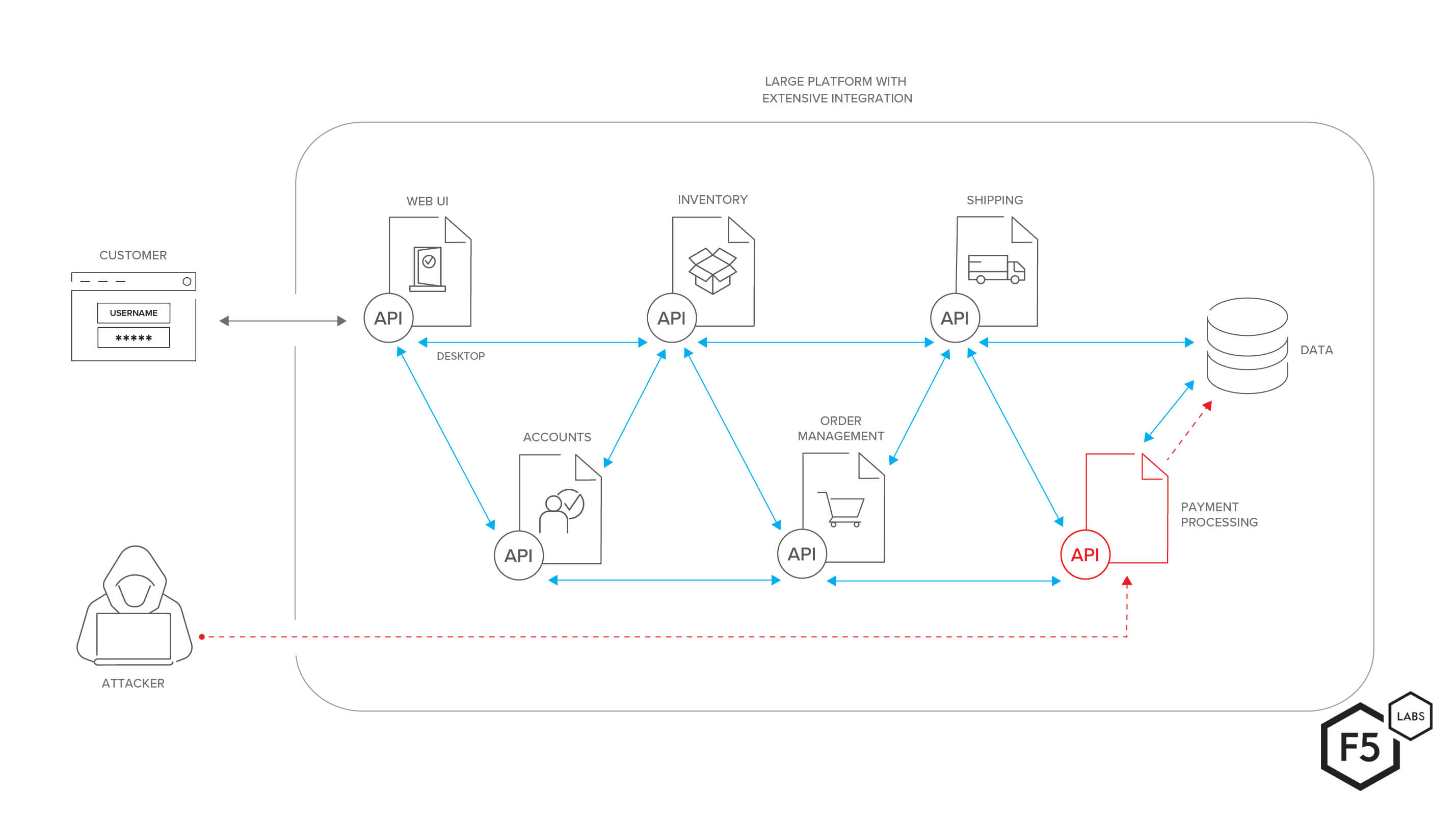
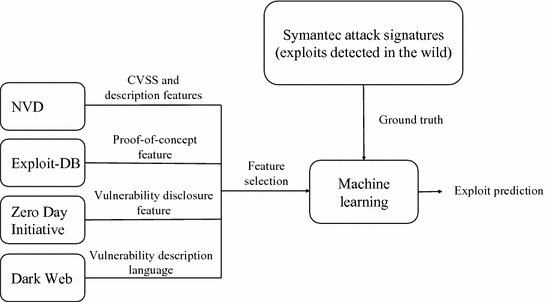
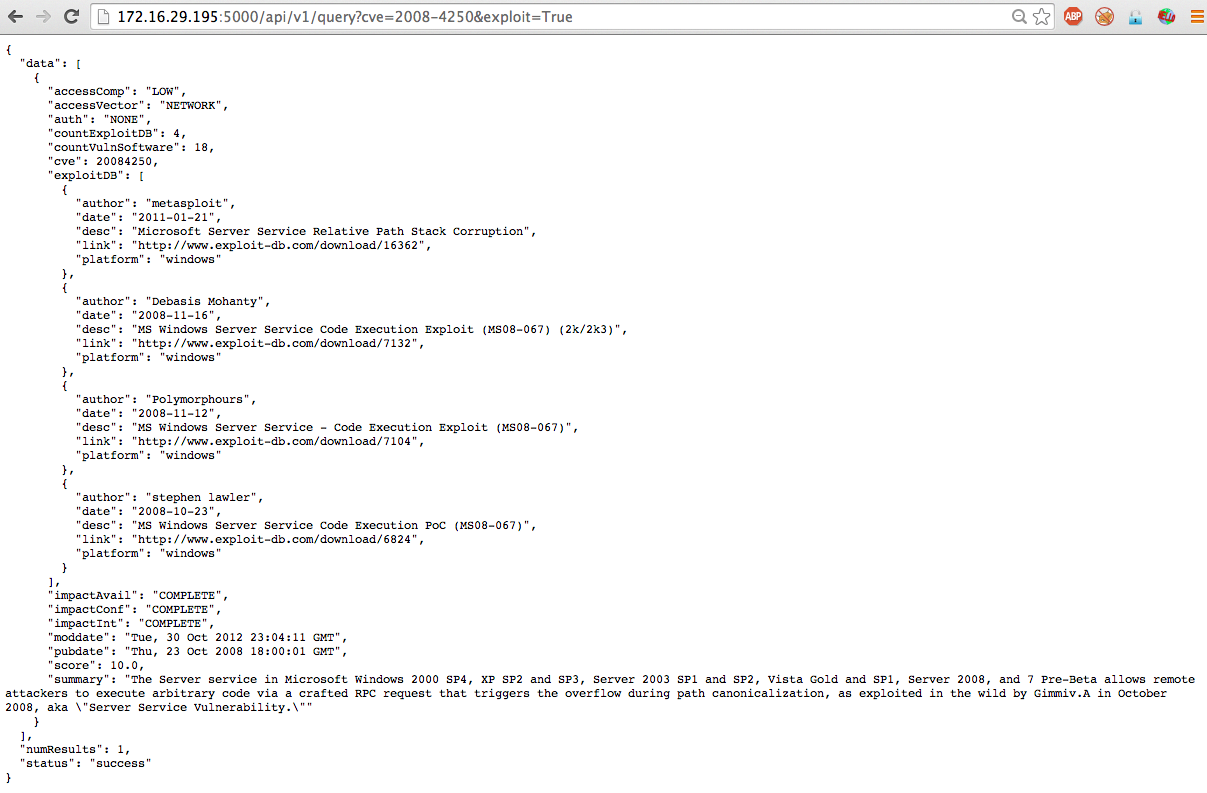
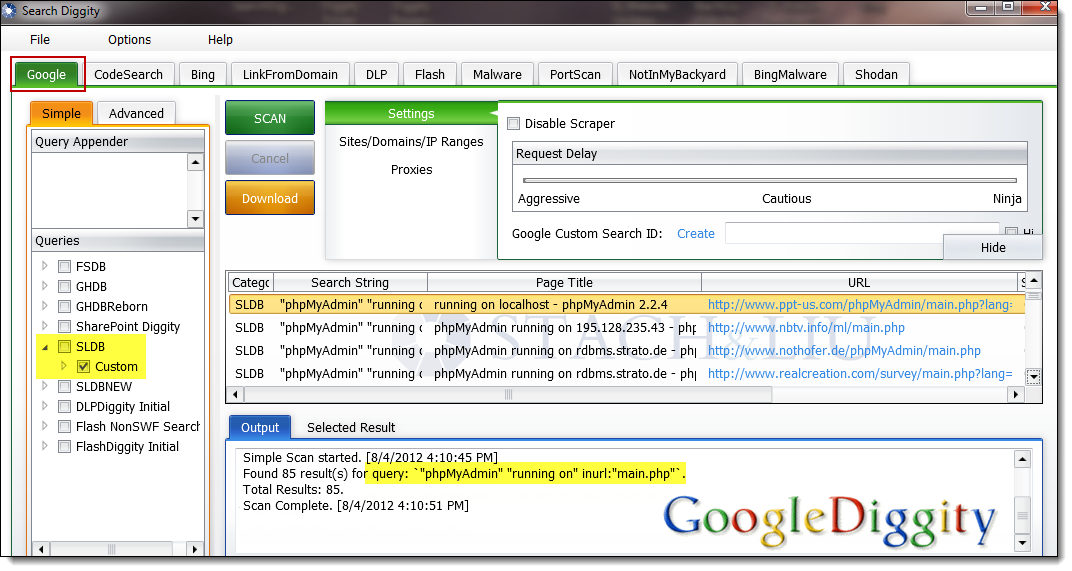
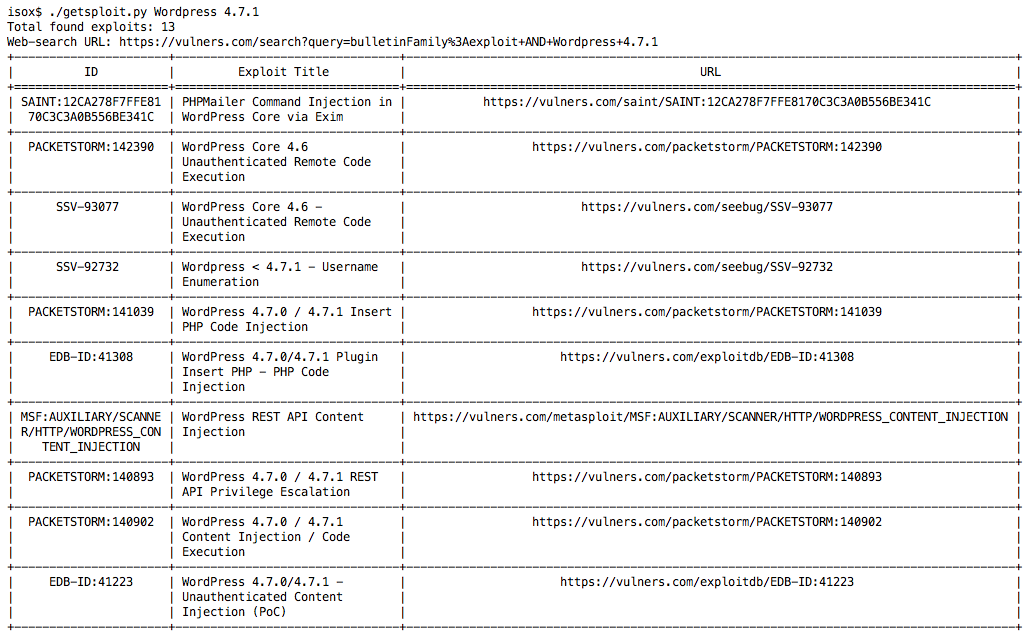
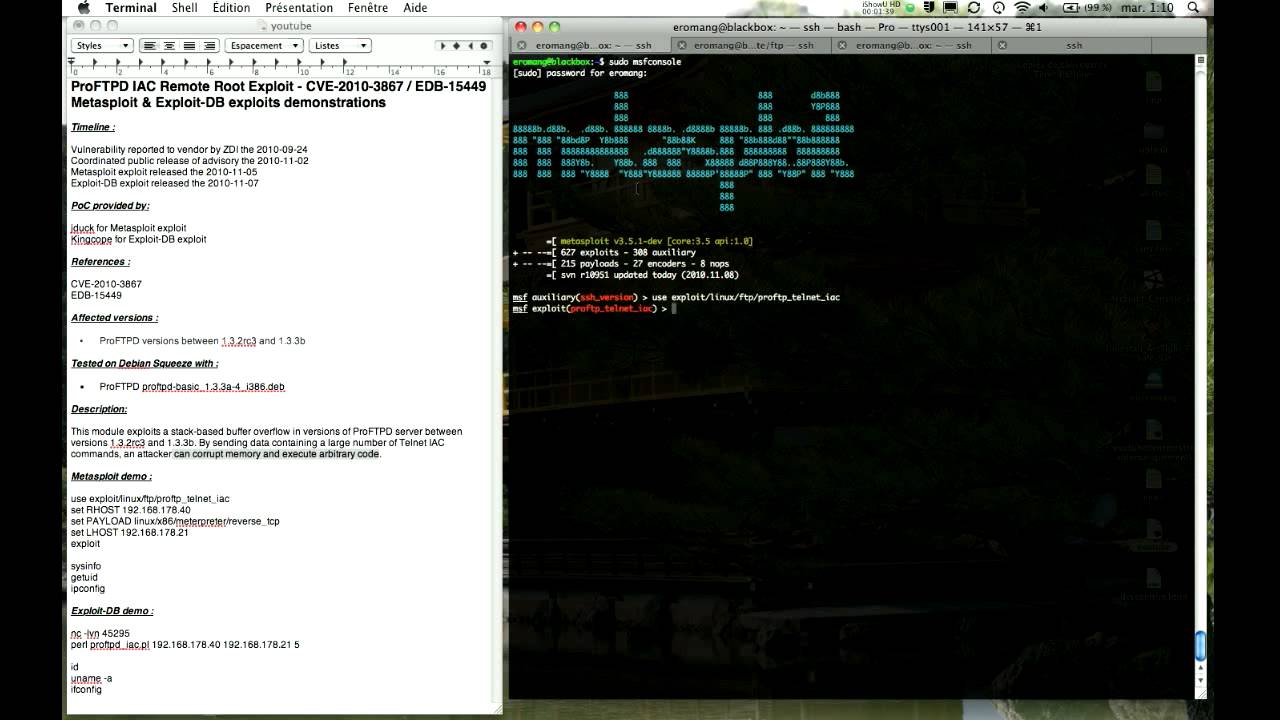
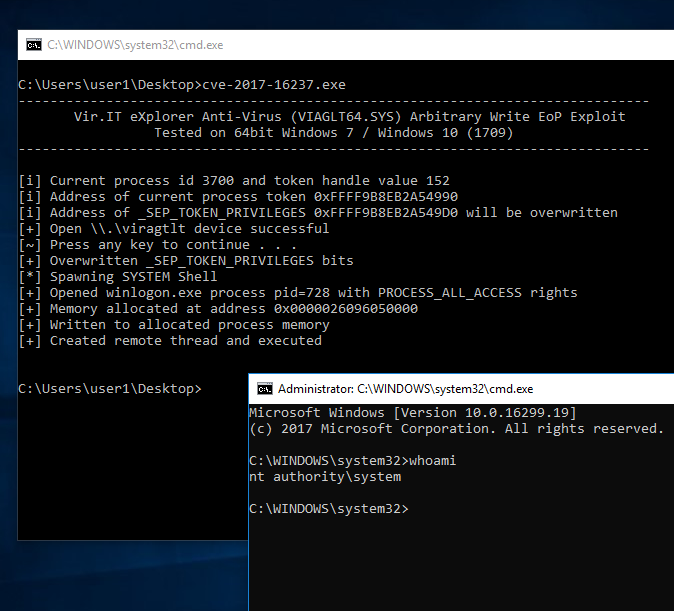
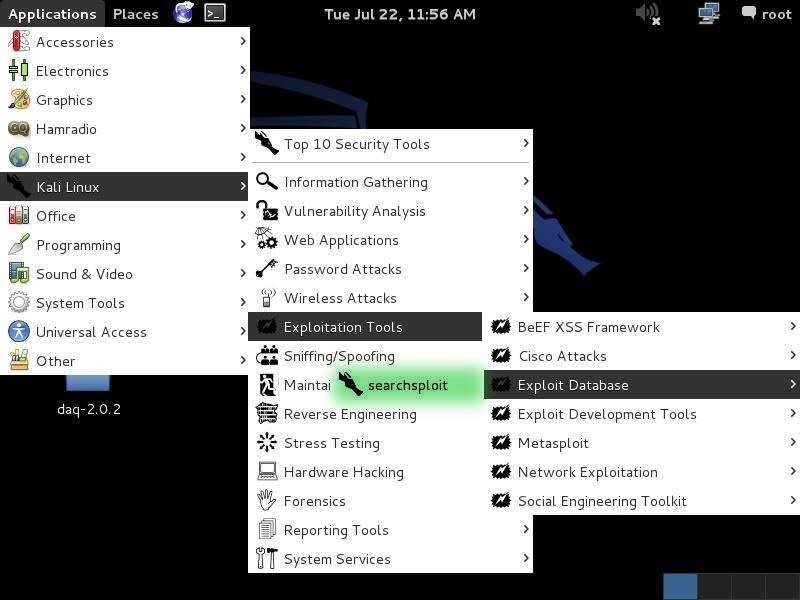
Exploit db api. Our aim is to serve the most comprehensive collection of exploits gathered through direct submissions mailing lists as well as other public sources and present them in a freely available and easy to navigate database. One of the most important and simple things your team should do to secure your api is to use https instead of http in your url. You can make exploits using what even some of the biggest exploit creators use. You can create your own custom commands with lua scripts.
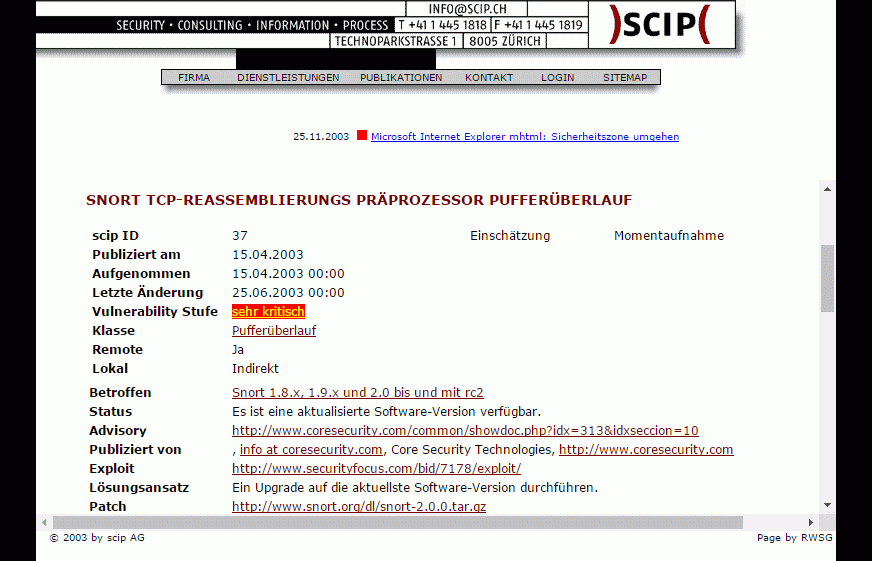
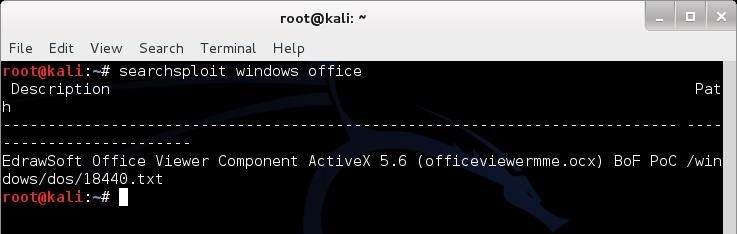
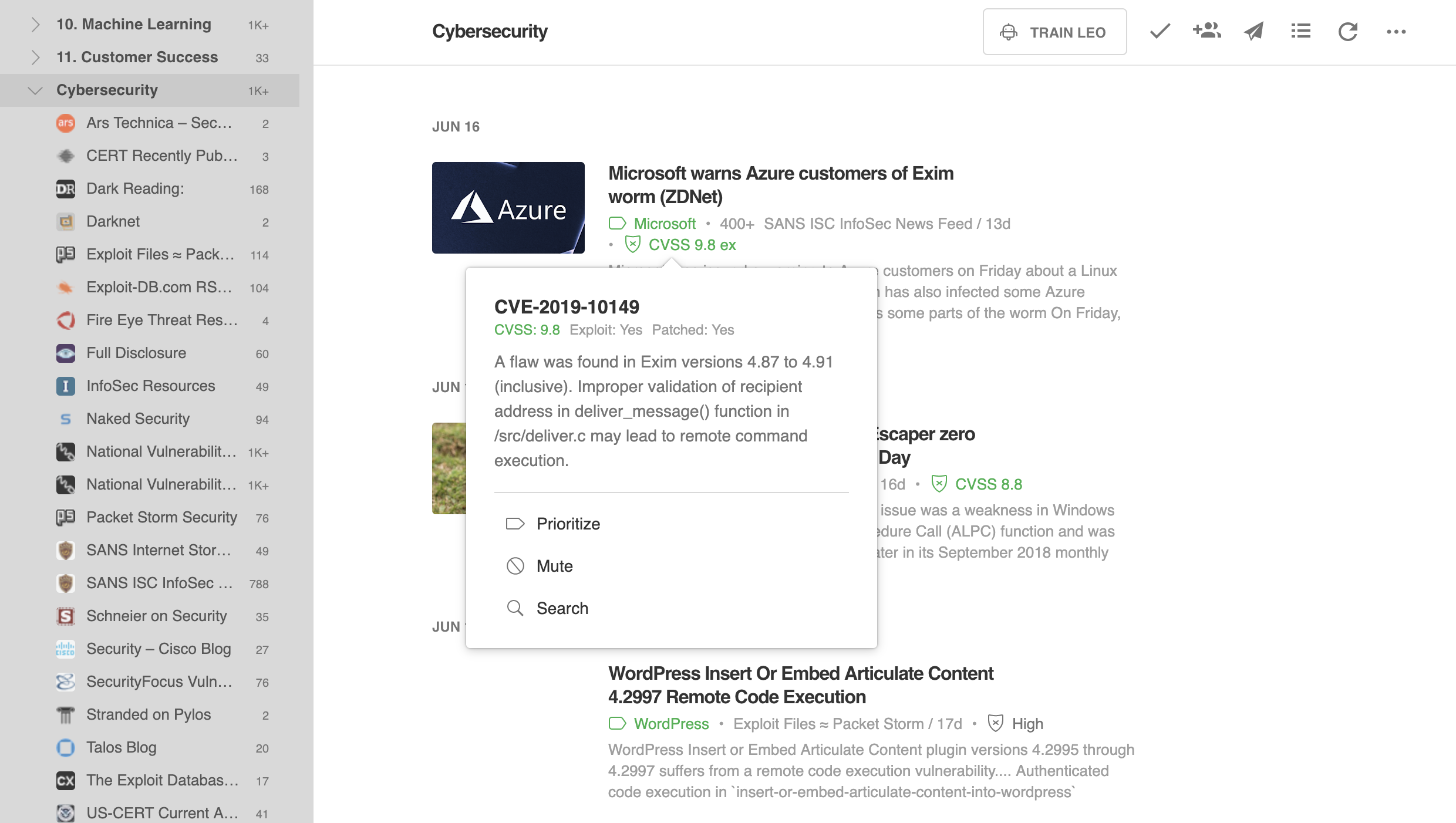
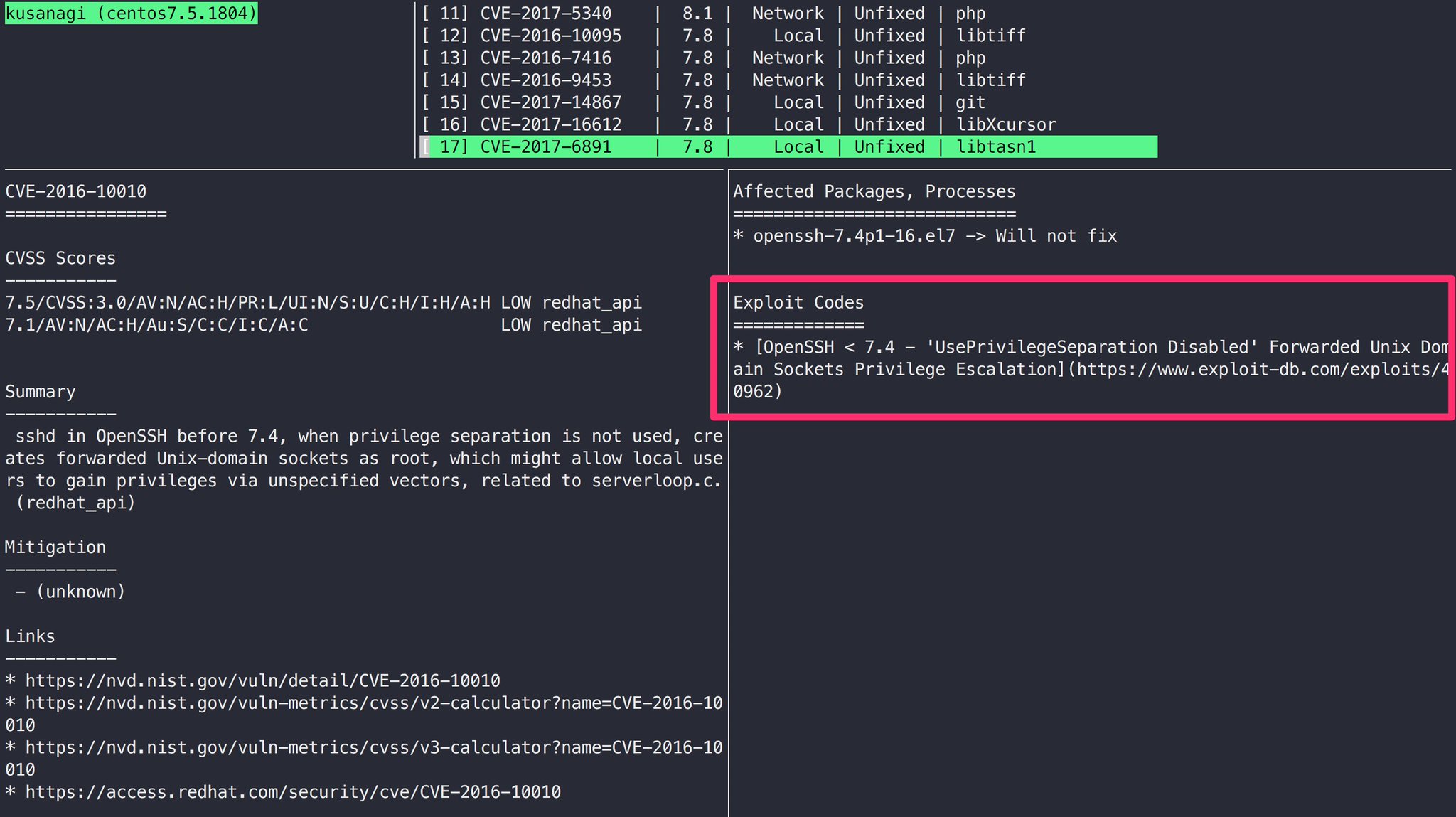
The exploit database is a non profit project that is provided as a public service by offensive security. In this day and age anyone can easily create one using our api. The exploit database is an archive of public exploits and corresponding vulnerable software developed for use by penetration testers and vulnerability researchers. Microsoft windows 10 theme api themepack file parsing.
The exploit database is a cve compliant archive of public exploits and corresponding vulnerable software developed for use by penetration testers and vulnerability researchers. The exploit database is a cve compliant archive of public exploits and corresponding vulnerable software developed for use by penetration testers and vulnerability researchers. Our aim is to serve the most comprehensive collection of exploits gathered through direct submissions mailing lists as well as other public sources and present them in a freely available and easy to navigate database. The exploit database is a cve compliant archive of public exploits and corresponding vulnerable software developed for use by penetration testers and vulnerability researchers.
Https encrypts the information sent between a user and a server. Youre given precoded commands. The exploit database is a cve compliant archive of public exploits and corresponding vulnerable software developed for use by penetration testers and vulnerability researchers. This approach protects sensitive information such as payment information usernames and mailing addresses.
Its aim is to serve as the most comprehensive collection of exploits shellcode and papers gathered through direct submissions mailing lists and other public sources and present them in a freely available and easy to navigate database. Insecure urls can easily be exploited. Mysql uroot createsql move or copy filescsv from exploitdb project in tmp and change the permissions to the file. The exploit database is maintained by offensive security an information security training company that provides various information security certifications as well as high end penetration testing services.